QRL JACKING
WHAT IS QRL JACKING ?
Qrljacking(Quick Response Code Login Jacking) is a simple social engineering attack vector capable of session hijacking affecting all applications that rely on “Login with QR code” feature as a secure way to login into accounts. In a simple way, In a nutshell victim scans the attacker’s QR code results of session hijacking.
HOW QRL JACKING IS WORKS?
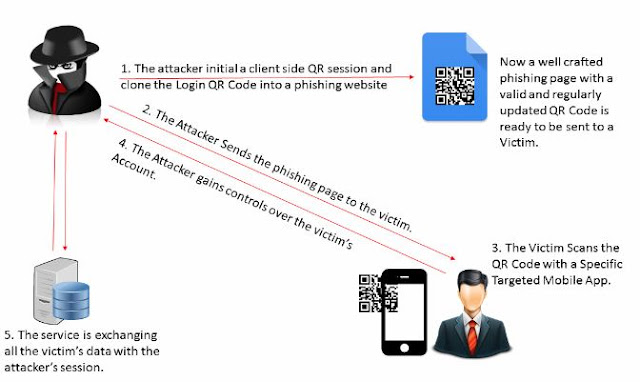
- The attacker generates a QR session and clones the Login QR code into a phishing website. Then the well-crafted phishing page with a valid and updated QR code is ready to be sent to the victim.
- After that, the attacker sends the phishing page to the victim by using his social engineering skills.
- The victim will scan the QR Code with a specific device.
- The attacker gains control of the victim’s account.
- The victim’s data is exchanged with the attacker’s session.
 |
| how qrl jacking works |
REQUIREMENTS TO ACHIEVE A SUCCESSFUL QRL JACKING
The QRL Jacking consists of two sides:
- Server Side: A server-side script is needed to serve and shape the final look to the victim.
- Client Side: Cloning the QR Code and pushing it to the phishing page.
VULNERABLE WEB APPLICATION AND SERVICES
There are a lot of well-known web applications and services which were vulnerable to this attack until the date we wrote this paper. Here are some examples
CHAT APPLICATIONS
Whatapp, QQ instant messaging, Weibo, Line, Wechat
MALING SERVIES
QQ mail, Yandex mail.
E-COMMERCE
Alibaba, Aliexpress, Tmall, Alimama, Taobao Trips
ONLINE BANKING
Alipay, Yandex money, Tenpay
OTHER SERVICES
Mydigipass, Zapper & Zapper WordPress login, Trustly App, Yelophone, Alibaba Yunos
QRL JACKING IMPLICATION
1. Accounts Hijacking
QRLJacking attack gives attackers the ability to apply a full account hijacking scenario on the vulnerable Login with QR Code feature resulting in accounts stealing and reputation affection.
2. Information Disclosure
When the victim scans the QR code he is giving the attacker much more information like for example (his accurate current GPS location, Device type, IMEI, SIM Card Information and any other sensitive information that the client application presents at the login process)
3. Callback Data Manipulation
When the attacker receives the data which we clarified in the “Information Disclosure” point, Some of this data is used to communicate with the service servers to clarify some information about the user which can be used later in the user’s application. Unfortunately sometimes this data is exchanged over insecure network connection which makes it easy for this data to be controlled by the attacker giving him the ability to alter or even remove it.
QRLJACKING AND ADVANCE REAL LIIFE ATTACK VECTORS
As we all know, If we combined more than one attack vector together we can have a great result. QRLJacking attack can be combined with a powerful attack vectors and techniques to make it more reliable and trustworthy
1. Social Engineering techniques (Targeted Attacks)
A skilled social engineer attacker will find this mission easy to convince the victim to scan the QR Code by cloning the whole web application login page with an exact one but with his own attacker side QR Code.
2. Hacked highly-trusted websites and services
Hacked websites are prone to be injected with a script that displays an Ad or a newly added section displays a cool offer if the user scanned this QR Code with a specific targeted mobile application his account will be hijacked.
3. SSL Stripping
SSL Stripping is an attack which is all about strip the ssl website and force it to work on a non secured version. Web sites without “HSTS Policy” enabled are prone to be stripped which gives the attacker multiple choices to manipulate the content of the website pages by for example, “altering the QR Code login sections”.
4. Content Delivery Networks (CDNs Downgrading)
A well implemented Login by QR Code feature uses a base64 QR code image generated and well placed in a secured page which will make it very difficult to be manipulated if this website is working over HTTPS and forcing HSTS, but unfortunately a lot of web applications and services uses a CDN based QR image generation process. These CDNs itself are sometimes stored on a servers vulnerable to HTTPS Downgrading attacks. Attackers will find a way to downgrade these secure connections, redirect the CDN URLs to his own QR Code, and since the QR Code is an image this will result in a “passive mixed content” hence the browser will not find any problems by viewing it on the web application login page instead of the original one.
5. Non-secure Traffic over LAN
This is the most suitable attack vector for attacking users over Local Area Networks by exploiting the non secured websites and manipulate traffic, The attacker here is performing MITM (Man in the Middle Attack) against his local area network, poisoning the traffic on the fly by injecting a JS file on every non secured web page.
6. Bad Implementation / Logic
Bad implementation logic of the QR code logins may result into a more easy accounts takeover scenarios. During our research we found a specific example: A chat app asks you to scan other people’s QR code to add them as friends, until here it's normal and there are no problems, but when it comes to the login process it’s a big problem. Unfortunately, the application implemented the “login by QR code” feature on the same screen that you’re using to add a friend, so imagine that someone cloned his login qr code and told you “Hey, This is my QR Code, scan it to be my friend, you scanned it, Boom” you lost your account.
DEFENDING AGAINST QRLJACKING
1. Session Confirmation, We recommend implementing a confirmation message/notification displaying characteristic information about the session made by the client/server.
2. IP Restrictions, Restricting any authentication process on different networks (WANs) will minimize the attack window.
3. Location-based Restrictions, Restricting any authentication process based on different locations will minimize the attack window.
4. Sound-based Authentication, One of the techniques to mitigate this kind of attack [And maintain the same usability level as to not require any additional interaction from the user other than scanning the QR ] is to add sound-based authentication step to the process , we have seen this kind of technology where it is possible to generate unique data and convert it to audio that can be recognized back into its original form [SlickLogin and Sound-Proof] so it is possible to include this technology in the process .
The purposes of this added step is to make sure that scanned QR code is generated in the same physical location as the mobile device that is doing the scan and therefore eliminating the possibility of a remote attacker deceiving the user into scanning his QR code.
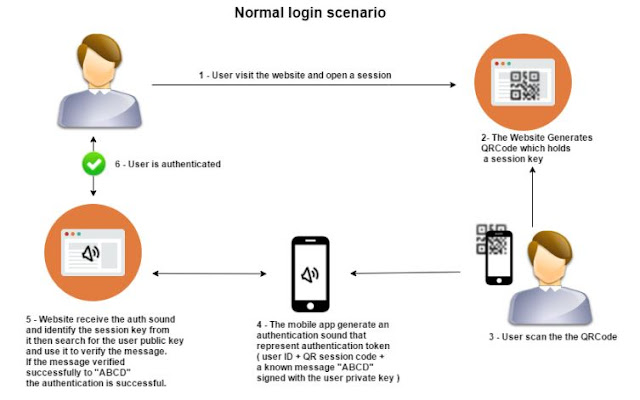 |
| NORMAL LOGIN SCENARIO |
The Attack Scenario: Attacker visits the website and opens a session.
1. The Website Generates QR Code which holds a session key.
2. Attacker crafts a phishing website with the received QR Code and sends it to the user.
3. User scans the attacker's QR Code in the phishing website.
4. The mobile App generates the authentication sound and play it to the phishing website.
5. The phishing website fails to process and capture the authentication audio as it requires additional browser permissions.
6. Even if the attacker tries to generate the authentication sound based on the (User ID) he still lacks the private key.
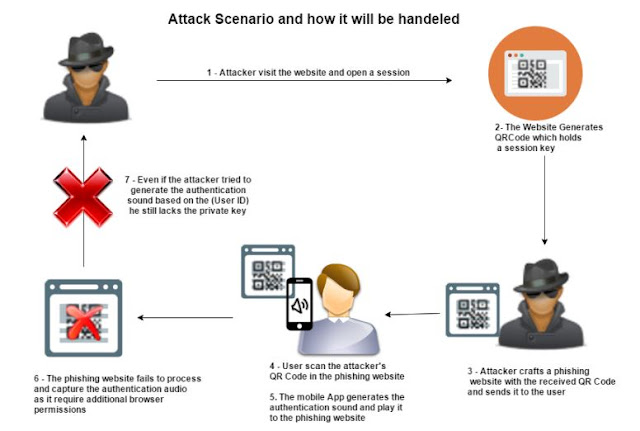 |
| ATTACK SCENARIO AND HOW IT WILL BE HANDELED |